- Connect to sqlplus: sqlplus => system => password1 OR sqlplus system/password1@sonlmdb
- Show current user: show user;
- Show current database: select * from global_name;
- OR select instance_name from v$instance;
- Create user: create user
identified by ; - Grant permission for user: grant connect,resource to
;
Tuesday, April 19, 2011
Oracle SQLPlus
Sunday, April 3, 2011
css & html tips
- Center align: margin-left: auto; margin-right: auto;
- html page always has toolbar: body { overflow-y: scroll; }
- Auto redirect to other page: META HTTP-EQUIV="Refresh" CONTENT="0; URL=html-redirect.html">
How to use SingTel BroadCom
2. An drive is mapped to your computer. Run the setup.exe file in there.
3. When be asked for prepaid or postpaid. Select post paid one.
4. Restart the computer
5. Wait for the driver to load completely then click on "Broad Band on Mobile" short cut on desktop.
6. Click connect and you're ready to use.
Friday, October 8, 2010
Tuesday, September 14, 2010
Wednesday, August 25, 2010
Monday, June 21, 2010
Sunday, May 2, 2010
Install eclipse plug-in
1. Find the URL of the plug-in (google)
2. Help --> Software Updates --> Add site button --> Paste URL
3. Select the plugin by checking the checkbox and then click Install
Saturday, March 27, 2010
Design icons for the application
- IcoFX: extract icons from resource/files of others application. They can be saved in .icon as well as image format.
- IconsExtractor: Use to search though the whole system to find icons and save to hard disk in .ico format.
Sunday, February 7, 2010
Oracle Administration
a. Open command prompt, change to C:\oracle\product\10.2.0\db_1\BIN>
b. set ORACLE_SID=cms
c. sqlplus / as sysdba;
d. create user
e. grant create session, connect, resource to emp_role, mgr_role;
f. Use sqldeveloper to connect to the schema to create table/view/store...
Saturday, January 23, 2010
MySQL
C:\mysql\bin>mysqld --remove uninstall mysql server
start mysql open windows services and start mysql
C:\mysql\bin>mysql Invoke mysql client
C:\mysql\bin>mysql -u root login to local mysql as root (default password is blank)
select version(), user();Check mysql version, current user
show databases; Show all databases
use New_DB_Name;Chang DB
CREATE USER 'user1'@'localhost' IDENTIFIED BY 'pass1';
grant all privileges on joomla.* to 'joomla'@'localhost';
CREATE DATABASE sonlmdb; create new db
mysql>use sonlmdb; select database
show tables;Show tables
describe tablename;show table's structure
connect to mysql by sqldeveloper
connect to mysql by using MySQL Query Browser
Create a new table: open MySQL Query Browser --> right click to the schema --> create new table
Execute scripts: connect by using sqldeveloper
show create table table_name\Gcreate table script
Generate schema's script: MySQL UI -> MySQL Administrator -> Backup
Monday, January 18, 2010
Character set vs. character encoding
Recently I was asked to explain the difference between character encoding and character set, and I thought it would be interesting to write about this over here as well.
In these two terms, ‘set’ refers to the set of characters and their numbers (code points), and ‘encoding’ refers to the representation of these code points. For example, Unicode is a character set, and UTF-8 and UTF-16 are different character encodings of Unicode.
To illustrate this difference, in the Unicode character set, the € character has code point 8364 (usually written as U+20AC, in hexadecimal notation). Using the UTF-16LE character encoding this is stored as AC 20, while UTF-16BE stores this as 20 AC, and the UTF-8 representation is E2 82 AC.
In practice however, the two terms are used interchangeably. The difference as described above is not applicable to most non-Unicode character sets (such as Latin-1 and SJIS) because their code points are the same as their encoding. Because of that, there has never been a real distinction from a historical perspective.
The most important difference in English is that the term character set is a little old fashioned, and character encoding is most commonly used nowadays. The reason for this is likely that it is more correct to speak of character encoding when UTF-8 and UTF-16 are different possible encodings.
Some examples:
* The HTTP protocol uses
Content-Type: text/html; charset=UTF-8
* The more recent XML uses
<?xml version="1.0" encoding="UTF-8"?>
This illustrates how they are used synonymously. Both describe the character encoding of the content that follows.
Saturday, January 2, 2010
vi useful shortcut keys
d$ delete to end of line
D delete to end of line
w move to next word (start)
e move to next word (end)
5w move 5 words and place cursor at first
5e move 4 words and place cursor at end
0 move to start of line
d5w delete 5 words
5dd delete 5 lines
Ctrl+R redo
ce change to end of word
c5e change 5 words
c$ change to end of line
C change to end of line
ctrl+G location in the file
gg move to start of file
% find matching ()[]
:! execute external command
v start select (virtual mode)
V start select whole line (virtual mode)
ctrl+v select rectangle
:w f write selection to file f
Y or yy copy current line
y copy the selection
d delete the selection
:r f insert text from f to this file
:r !ls put the ls output to current line
o open line below cursor
y5w yank 5 words
:set is set incrimental search
:help help
: ctrl+D possible completions
fa move to first 'a' character
ta move to before first 'a' character
dfa delete until the first 'a' character
cc clear current line and enter insert mode
S clear current line and enter insert mode
ma bookmark 'a' for the position
'a go to bookmark 'a'
'. go to last modification
HML jump to top/middle/last line of the screen
J join current lines
~ toggle case
* find the word under cursor.
. repeat last changing.
--jump-target position target line on line num of screen.
Sunday, November 29, 2009
Linux command
ls -lht
-l: long format
-h: human readable size (ex: 2k, 2M,..)
-t: sort by time (default = sort by name)
* Count number of line in file
wl -l filename
* Get last 100 line of a file and numbering
tail -100 source | nl > dest
* Remove whole directory and all files inside
rm -r folder_name
-r: recursive
* Backup a folder
tar -cvf file.tar folder_name
* Extract a file
tar -xvf file.tar
* Disk use:
du - sh
-s: only total sum
-h: size human format
du | sort -n (unix)
du | sort -g (fedora)
* Install package
sudo apt-get install vim-runtime
* Check disk space
df -h
* Check memory
prstat -a
vmstat
* Find file
find / -name filepattern
locate filepattern
* Mound a pen drive
mount /dev/sda1 /mnt/usbdisk
* Change mode
chmod ugo+rwx directory1
* Find text in files
find . -type f -exec grep "pattern" {} \;
* Make a pdf of a manual page
man -t man |ps2pdf - > man.pdf
* Go to previous directory
cd -
Thursday, November 26, 2009
IE security settings

General
- .Net framework: related to .NET itself
- .Net framework-reliant component: related to component which is developed base on .NET
- ActiveX control and plug-ins: (ActiveX = Java applets)
- Download: file and font download setting
- Enable .NET framework setup: .NET framework again.
- Scripting: Control script langauge (ex: javascript)
- User authentication: auto log on machenics
- Miscelaneous: Not belong to any categories
Miscelaneous
- Access data sources cross domain: ???
- Allow META REFRESH: a method of instructing a web browser to automatically refresh the current web page or frame after a given time interval.
Monday, November 23, 2009
Sunday, November 22, 2009
Insert checkbox to Excel 2010 (2007)
- Display the Developer tab
- Click Microsoft Office Button and then click Excel Option.
- Click Customize Ribbon in the Left Pannel
- Select "Main Tabs" Ribbon below "Customize the Ribbons"
- Check in to Developer checkbox
- Click OK to save your change
- Click on Developer tab
- Click Insert button on Rubbon to insert form controls: checkbox/radio/...



Thursday, November 19, 2009
Some Oracle queries
- List all tables: select * from tab;
- Print database name: select ora_database_name from dual;
- Run a script file: SQL> @/oracle/scripts/script.sql
Oracle error: java.lang.Exception: Exception in sending Request :: null
In our case it was: agentTZregion=Singapore (for a list of supported region, refer to oracle\product\10.2.0\db_1\sysman\admin\supportedtzs.lst file)
Reboot and watch dbconsole work.
Thursday, November 12, 2009
How to extend your monitor over two laptops
- You don't want to waste the other monitor when using remote desktop.
- You don't want to continuously leave and grab mouse.
Question: how to extend the monitor? Then, when I move the mouse over the edge of the primary screen, the mouse will move to the screen of the secondary laptop. Below is my solution for doing that. You need to tools (all free) to do this.
- Download and run TightVNC on the secondary laptop. This will be the VNC server.
- Run TightVNC as a Viewer on the primary laptop and connect to the secondary one
- Extend your primary laptop by using Projector mode (for Windows 7, press Win+P)
- Now, move your VNC Viewer window to the extended area of the primary laptop. You will not able to see the VNC Viewer windows. But when you move your mouse over the hidden area, you can see the mouse in the secondary laptop's screen.
- Now, it's nearly done. Except that when you maximize a windows in primary laptop, the VNC automatically minimize to the taskbar. To prevent this, install the OnTop utility and make the VNC Viewer ontop of all windows.
Wednesday, November 11, 2009
windows 7 activation keys
Monday, November 9, 2009
Sunday, November 8, 2009
Remove in xml/html file
Replace by empty
Regular Expression: Yes
Option: - Multiline: Yes; Single line: Yes
Thursday, November 5, 2009
Basic config mail server (James)
<?xml version="1.0"?>
<!DOCTYPE config [
<!ENTITY fetchmailConfig SYSTEM "../conf/james-fetchmail.xml">
]>
<config>
<James>
<postmaster>error@sonle.com</postmaster>
<servernames autodetect="false" autodetectIP="false">
<servername>sonle.com</servername>
</servernames>
<usernames ignoreCase="true" enableAliases="true" enableForwarding="true"/>
<inboxRepository>
<repository destinationURL="file://var/mail/inboxes/" type="MAIL"/>
</inboxRepository>
</James>
&fetchmailConfig;
<mailetpackages>
<mailetpackage>org.apache.james.transport.mailets</mailetpackage>
<mailetpackage>org.apache.james.transport.mailets.smime</mailetpackage>
</mailetpackages>
<matcherpackages>
<matcherpackage>org.apache.james.transport.matchers</matcherpackage>
<matcherpackage>org.apache.james.transport.matchers.smime</matcherpackage>
</matcherpackages>
<spoolmanager>
<threads> 10 </threads>
<processor name="root">
<mailet match="All" class="PostmasterAlias"/>
<mailet match="RelayLimit=30" class="Null"/>
<mailet match="HasMailAttributeWithValue=org.apache.james.infected, true" class="ToProcessor">
<processor> virus </processor>
</mailet>
<mailet match="HasMailAttribute=spamChecked" class="ToProcessor">
<processor> transport </processor>
</mailet>
<mailet match="All" class="SetMailAttribute">
<spamChecked>true</spamChecked>
</mailet>
<mailet match="SMTPAuthSuccessful" class="ToProcessor">
<processor> transport </processor>
</mailet>
<mailet match="InSpammerBlacklist=query.bondedsender.org."
class="ToProcessor">
<processor> transport </processor>
</mailet>
<mailet match="InSpammerBlacklist=dnsbl.njabl.org."
class="ToProcessor">
<processor> spam </processor>
<notice>550 Requested action not taken: rejected - see http://njabl.org/ </notice>
</mailet>
<mailet match="All" class="ToProcessor">
<processor> transport </processor>
</mailet>
</processor>
<processor name="error">
<mailet match="All" class="ToRepository">
<repositoryPath> file://var/mail/error/</repositoryPath>
</mailet>
</processor>
<processor name="transport">
<mailet match="SMTPAuthSuccessful" class="SetMimeHeader">
<name>X-UserIsAuth</name>
<value>true</value>
</mailet>
<mailet match="HasMailAttribute=org.apache.james.SMIMECheckSignature" class="SetMimeHeader">
<name>X-WasSigned</name>
<value>true</value>
</mailet>
<mailet match="RecipientIsLocal" class="LocalDelivery"/>
<mailet match="HostIsLocal" class="ToProcessor">
<processor> local-address-error </processor>
<notice>550 - Requested action not taken: no such user here</notice>
</mailet>
<mailet match="RemoteAddrNotInNetwork=127.0.0.1" class="ToProcessor">
<processor> relay-denied </processor>
<notice>550 - Requested action not taken: relaying denied</notice>
</mailet>
<mailet match="All" class="RemoteDelivery">
<outgoing> file://var/mail/outgoing/ </outgoing>
<delayTime> 5 minutes </delayTime>
<delayTime> 10 minutes </delayTime>
<delayTime> 45 minutes </delayTime>
<delayTime> 2 hours </delayTime>
<delayTime> 3 hours </delayTime>
<delayTime> 6 hours </delayTime>
<maxRetries> 25 </maxRetries>
<deliveryThreads> 1 </deliveryThreads>
<sendpartial>false</sendpartial>
<bounceProcessor>bounces</bounceProcessor>
</mailet>
</processor>
<processor name="spam">
<mailet match="All" class="ToRepository">
<repositoryPath>file://var/mail/spam/</repositoryPath>
</mailet>
</processor>
<processor name="virus">
<mailet match="All" class="SetMailAttribute">
<org.apache.james.infected>true, bouncing</org.apache.james.infected>
</mailet>
<mailet match="SMTPAuthSuccessful" class="Bounce">
<inline>heads</inline>
<attachment>none</attachment>
<notice> Warning: We were unable to deliver the message below because it was found infected by virus(es). </notice>
</mailet>
<mailet match="All" class="Null" />
</processor>
<processor name="local-address-error">
<mailet match="All" class="ToRepository">
<repositoryPath> file://var/mail/address-error/ </repositoryPath>
</mailet>
</processor>
<processor name="relay-denied">
<mailet match="All" class="ToRepository">
<repositoryPath>file://var/mail/relay-denied/</repositoryPath>
</mailet>
</processor>
<processor name="bounces">
<mailet match="All" class="DSNBounce">
<passThrough>false</passThrough>
</mailet>
</processor>
</spoolmanager>
<dnsserver>
<servers>
</servers>
<autodiscover>true</autodiscover>
<authoritative>true</authoritative>
<maxcachesize>50000</maxcachesize>
</dnsserver>
<remotemanager enabled="true">
<port>4555</port>
<handler>
<helloName autodetect="true">sgsv-minhle01</helloName>
<administrator_accounts>
<account login="root" password="root"/>
</administrator_accounts>
<connectiontimeout> 60000 </connectiontimeout>
<prompt>james></prompt>
</handler>
</remotemanager>
<pop3server enabled="true">
<port>110</port>
<handler>
<helloName autodetect="true">sgsv-minhle01</helloName>
<connectiontimeout>120000</connectiontimeout>
</handler>
</pop3server>
<smtpserver enabled="true">
<port>25</port>
<handler>
<helloName autodetect="true">sgsv-minhle01</helloName>
<connectiontimeout>360000</connectiontimeout>
<authRequired>true</authRequired>
<maxmessagesize>0</maxmessagesize>
</handler>
</smtpserver>
<nntpserver enabled="false">
</nntpserver>
<nntp-repository>
<readOnly>false</readOnly>
<rootPath>file://var/nntp/groups</rootPath>
<tempPath>file://var/nntp/temp</tempPath>
<articleIDPath>file://var/nntp/articleid</articleIDPath>
<articleIDDomainSuffix>news.james.apache.org</articleIDDomainSuffix>
<newsgroups>
<newsgroup>org.apache.avalon.user</newsgroup>
</newsgroups>
<spool>
<configuration>
<spoolPath>file://var/nntp/spool</spoolPath>
<threadCount>1</threadCount>
<threadIdleTime>60000</threadIdleTime>
</configuration>
</spool>
</nntp-repository>
<spoolrepository destinationURL="file://var/mail/spool/" type="SPOOL"/>
<mailstore>
<repositories>
<repository class="org.apache.james.mailrepository.AvalonMailRepository">
<protocols>
<protocol>file</protocol>
</protocols>
<types>
<type>MAIL</type>
</types>
</repository>
<repository class="org.apache.james.mailrepository.AvalonSpoolRepository">
<protocols>
<protocol>file</protocol>
</protocols>
<types>
<type>SPOOL</type>
</types>
</repository>
<repository class="org.apache.james.mailrepository.filepair.File_Persistent_Object_Repository">
<protocols>
<protocol>file</protocol>
</protocols>
<types>
<type>OBJECT</type>
</types>
<models>
<model>SYNCHRONOUS</model>
<model>ASYNCHRONOUS</model>
<model>CACHE</model>
</models>
</repository>
<repository class="org.apache.james.mailrepository.filepair.File_Persistent_Stream_Repository">
<protocols>
<protocol>file</protocol>
</protocols>
<types>
<type>STREAM</type>
</types>
<models>
<model>SYNCHRONOUS</model>
<model>ASYNCHRONOUS</model>
<model>CACHE</model>
</models>
</repository>
</repositories>
</mailstore>
<users-store>
<repository name="LocalUsers" class="org.apache.james.userrepository.UsersFileRepository">
<destination URL="file://var/users/"/>
</repository>
</users-store>
<database-connections>
</database-connections>
<connections>
<idle-timeout>300000</idle-timeout>
<max-connections>30</max-connections>
</connections>
<sockets>
<server-sockets>
<factory name="plain" class="org.apache.avalon.cornerstone.blocks.sockets.DefaultServerSocketFactory"/>
</server-sockets>
<client-sockets>
<factory name="plain" class="org.apache.avalon.cornerstone.blocks.sockets.DefaultSocketFactory"/>
</client-sockets>
</sockets>
<thread-manager>
<thread-group>
<name>default</name>
<priority>5</priority>
<is-daemon>false</is-daemon>
<max-threads>100</max-threads>
<min-threads>20</min-threads>
<min-spare-threads>20</min-spare-threads>
</thread-group>
</thread-manager>
</config>
How to backup Oracle database
- Export full database
- Example of Exporting Schemas
- Exporting Individual Tables
- Using Import Utility
- IMP KEYWORD=value or KEYWORD=(value1,value2,...,valueN)
The above command will export all the objects stored in SCOTT and ALI’s schema.
This will export scott’s emp and sales tables.
USERID must be the first parameter on the command line.
Wednesday, November 4, 2009
How to setup email section in weblogic
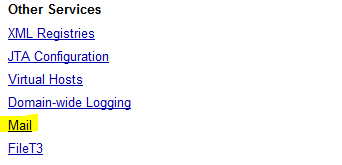
Click on Mail link below Other services section
Click "Configure a New Mail Section"
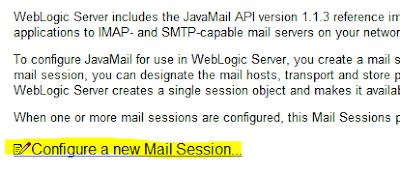
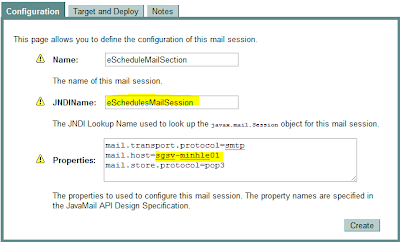
Enter the mail section information.
- JNDI name is used for reference in souce code
- Host name is the mail server name
Click Apply button
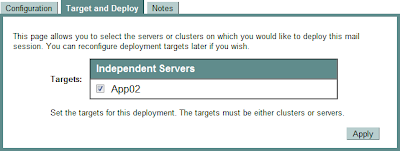
Select an application to deploy to.
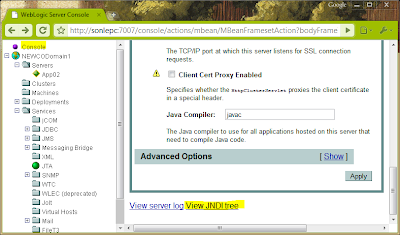
Verify steps:
- Click on the Console link on the left panel
- Click on the View JNDI tree
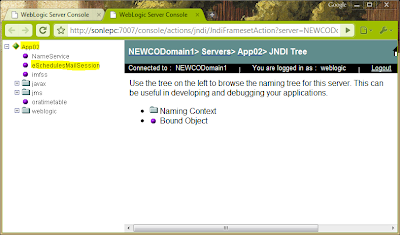
The created email section should be displayed on the left panel
NirSoft
- mailpv - view mail client password
- SkypeLogView - view Skype log without login
- SiteShoter - a small utility that allows you to save a screenshot of any Web page into a file
- HtmlDocEdit - Simple editor/designer for HTML files
- PasswordFox - Reveal the user names/passwords stored in Firefox
- ChromePass - Chrome Browser Password Recovery
- Asterisk Logger - Reveal/recover/monitor password behind asterisks ...
- AsterWin IE - Reveal asterisk passwords in Internet Explorer
- WirelessNetView - View the wireless sysnal around you
- SmartSniff - a network monitoring utility that allows you to capture TCP/IP packets that pass through your network adapter
- ServiWin - utility displays the list of installed drivers and services on your system.
- RunAsDate - a small utility that allows you to run a program in the date and time that you specify
- rdpv - remote desktop passview
- ProcessActivityView - is supposed to give you a summary of the files and folders being accessed by a specific process
- OpenedFilesView - View opened/locked files in your system
- Netpass - recovers all network passwords stored on your system for the current logged-on user
- MyLastSearch - utility scans the cache and history files of your Web browser, and locate all search queries that you made with the most popular search engines
- MyEventViewer – alternative utility for Windows logs
- MessenPass - Instant Messenger Password Recovery Tool
- MozillaHistoryView - View the list of visited web sites in Firefox
- MozillaCacheView - View the cache files of Firefox/Mozilla browsers
- IE PassView - Password Manager Program for Internet Explorer
- IE HistoryView: Freeware Internet Explorer History Viewer
- IECacheView - Internet Explorer Cache Viewer
- GACView - Alternative Global Assembly Cache (GAC) Viewer
- DriverView - Loaded Windows Drivers List
- Dialupassw2: Recover lost dialup/RAS/VPN password in Windows XP/Vista/9x
- cports: Monitoring TCP/IP network connections on Windows
- CleanAfterMe - Clean Registry entries and files in your system
- AsterWin IE - Reveal asterisk passwords in Internet Explorer
- NirCmd DLL is a sample dll that you can call in order to execute NirCmd Commands.
Tuesday, November 3, 2009
Build up a mail server/client for tesing purpose
- Download James and extract to a local folder.
- Open Jame-x.y.z\apps\james\SAR-INF\config.xml to configure mail server as follow:
- <servername>sonle.com</servername>. This can be not the same as your computer name. (My email has xxx@sonle.com format in this example)
- <helloName autodetect="true">sonle.com</helloName>. There are more than one place for you to set this value.
- Start server: double click to run file james-x.y.z\bin\run.bat
- Add accounts
- Open command line
- issue command telnet [computername] 4555
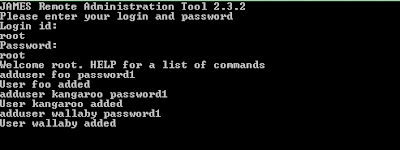
- When you are asked for userid and password, enter root for both username and password (which is the defalt value in config.xml file
- adduser [username] [password]
- Repeat the adduser to add as many users as you like. After finish, type quit to exit the telnet.
- Now, the server is ready. It's time to setup a client to test mail server by user the mail accounts you just created
- Download Thunderbird and install to your machine. I prefer this tool because it's lightweight, fast and free!
- Open Thunderbird. Since the first time, you will be asked for setting up email account. Just lick Ok to accept.

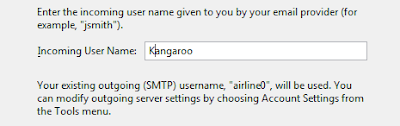
- Enter name and email address which is setup before.

- Enter your machine name where you setup James. If you not sure what to enter, go to commandline and type: ipconfig/all to get the name.
Remember to uncheck the checkbox. It's clearer to setup each account on a separated folder.

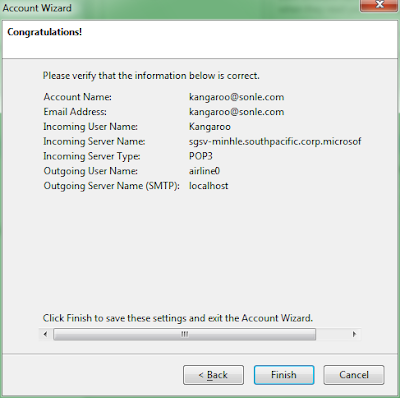
Click finish to complete setting up mail client.
Repleat your steps until you have already add all your account to Thunderbird. Now try to send and email to see whether the mail server is working already.
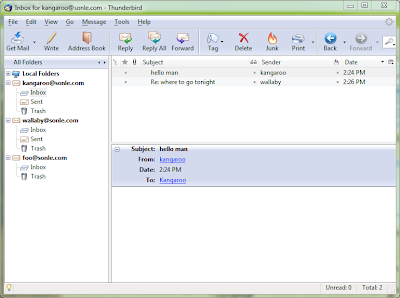
* Notice: When you want to add an account to ThunderBird, open File --> New --> Account, and thing will be fine.
If you go to Tools --> Account Settings and click the button "Add Account..." Then, if you uncheck the check box "Use Global Inbox" --> There is an error when receive POP email.
How to recover email password
- Mail PassView - Recover passwords stored in Email clients (Outlook, Windows Live Mail, Thunderbird, and so on).
- Asterisk Logger - Recover passwords stored behind asterisk (**) characters.
Monday, November 2, 2009
Shortcut keys
- Ctrl+U - View source
- Ctrl+Shift+V – Paste current content from the clipboard without formatting
- Ctrl+L or Alt+D - Highlight URL
- Ctrl+Backspace - Fast delete
- Shift & wheel - Scrolls horizontally on the page
- Win+Left: Move windows to half left of the screen
- Win+Right: Move windows to half right of the screen
- Win+Up: Maximize the windows
- Win+P: Projector mode
- Ctrl+Shift+P: Find matched braces
- Alt+Shift+P: Select the outer block
- Ctrl+Shift+R: Open resource
- Alt+Shift+W: Open file in Navigator/Project Explorer/...
- CTRL+P: Copy current path to cmd line
- Ctrl+Shift+Ins: Copy file path to clipboard
Friday, October 30, 2009
Serialize Object To File
using System.IO;
using System.Xml.Serialization;
public void SerializeObject(string filename, PersonnelService.PersonnelInput objectToSerialize)
{
Stream stream = File.Open(filename, FileMode.Create);
XmlSerializer ser = new XmlSerializer(typeof(PersonnelService.PersonnelInput));
ser.Serialize(stream, objectToSerialize);
stream.Close();
}
Thursday, October 29, 2009
Wednesday, October 28, 2009
How to deploy a web application to Weblogic
Tuesday, October 27, 2009
Ringtone converter: from and to .amr file
Saturday, October 24, 2009
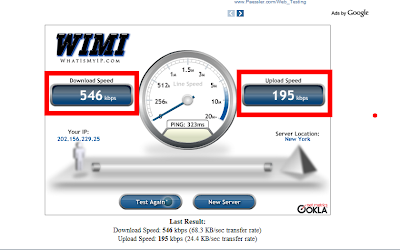
How to know the web server type
Want to know where is the location of a server
How to test your internet speed
2. Choose a server and click test
3. Wait for about less than 1 minute and see the result
Thursday, October 22, 2009
Oracle - Add new column to a table
ADD ( "TEAM" VARCHAR2(2) DEFAULT 'AT' )
Wednesday, October 21, 2009
Common processes
The process lsass.exe serves as the Local Security Authentication Server by Microsoft, Inc. It is responsible for the enforcement of the security policy within the operating system. This process checks whether a user’s supplied identification is valid or not whenever he or she tries to access the computer system.
With the execution of the file lsass.exe, the system acquires security by preventing the access of unwanted users to any private information. The file lsass.exe also handles the password modifications done by the user.
Local Session Manager. Process found on Windows Vista and whose role is to manage the terminal server connections to the machine. In Vista, terminal server sessions are not just Remote Desktop sessions from remote users as they are in Windows XP/2003, they are also your sessions when you are logged in to the PC at the PC itself, as all sessions, whether local or remote, are virtualised terminal server sessions. It follows, therefore, that this process is a crucial core process of Windows Vista.
is a process belonging to the Windows login manager. It handles the login and logout procedures on your system. This program is important for the stable and secure running of your computer and should not be terminated
is a part of the Microsoft Windows Operating System and manages the operation of starting and stopping services. This process also deals with the automatic starting of services during the computers boot-up and the stopping of services during shut-down. This program is important for the stable and secure running of your computer and should not be terminated.
This is a system critical process, as long as it exists in %windir%\system32. Its job is to start some of the core Windows Vista background services.
The Microsoft Client Server Runtime Server subsystem utilizes the process csrss.exe for managing the majority of the graphical instruction sets under the Microsoft Windows operating system. As such Csrss.exe provides the critical functions of the operating system, and its termination can result in the Blue Screen of Death being displayed.
Csrss.exe controls threading and Win32 console window features. Threading is where the application splits itself into multiple simultaneous running tasks. Threads supported by csrss.exe are different from processes in that threads are commonly contained within the process, with various threads sharing resources within the same process. The Win32 console is the plain text window in the Windows API system (programs can use the console without the need for image display).
In mobile devices such as notebooks and laptops, the process csrss.exe is closely dependent on power management schemes implemented by the system as defined under the Control Panel option.
The Session Manager Subsystem is responsible for starting a user's session. When this process begins, the system thread is responsible for a number of specific tasks including launching the Winlogon, specific Win32 processes and among other items, setting the system variables.
Many computer users first notice the SMSS.exe process when a system shuts down abnormally. For instance, when a Winlogon ends normally, this process usually has no problem fulfilling its tasks, however, when a system shuts down abnormally or unexpectedly, the SMSS.exe causes a "hang" which is when the system stops responding.
Tuesday, October 20, 2009
Screen recorder
2. Screen capture

3. Download link:
- From wareseeker: http://wareseeker.com/download/oripa-screen-recorder-1.2.2.rar/416172
- I've downloaded and uploaded to the following location: http://cid-194a44aed6d769a5.skydrive.live.com/self.aspx/.Public/oRipa%5E_Screen%5E_Recorder.msi
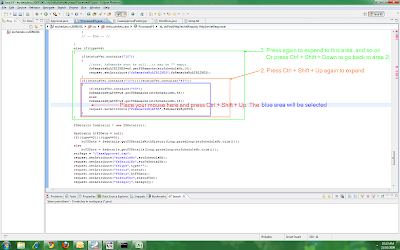
Eclipse - how to select enclosed element
2. Press Alt + Shift + Up to expand the selection
3. Press Alt + Shift + Down to collapse the selection
* The image below is wrong (Alt instead of Ctrl)
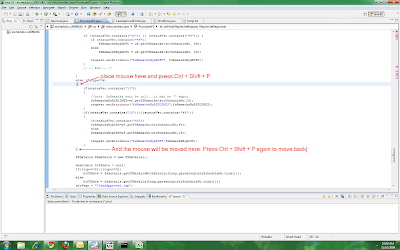
Eclipse - how to find the match brace
2. Press Ctrl + Shift + P to jump to the match brace
3. Press Ctrl + Shift + P again to jump back.
Monday, October 19, 2009
Useful windows command
- http://commandwindows.com/doskey.htm
- tasklist /svc list all services which are running
- netstat -n -a list all port which are in using
- msinfo32 system information
- tracert The actual path between two computers on the Internet
- pathping combine ping and tracert
- nslookup diagnose the Domain Name System (DNS) infrastructure and comes with a number of sub-commands
- netsh The network services shell is a large suite of many tools
What is svchost.exe And Why Is It Running?
What is svchost.exe And Why Is It Running?
You are no doubt reading this article because you are wondering why on earth there are nearly a dozen processes running with the name svchost.exe. You can’t kill them, and you don’t remember starting them… so what are they?
So What Is It?
According to Microsoft: “svchost.exe is a generic host process name for services that run from dynamic-link libraries”. Could we have that in english please?
Some time ago, Microsoft started moving all of the functionality from internal Windows services into .dll files instead of .exe files. From a programming perspective this makes more sense for reusability… but the problem is that you can’t launch a .dll file directly from Windows, it has to be loaded up from a running executable (.exe). Thus the svchost.exe process was born.
Why Are There So Many svchost.exes Running?
If you’ve ever taken a look at the Services section in control panel you might notice that there are a Lot of services required by Windows. If every single service ran under a single svchost.exe instance, a failure in one might bring down all of Windows… so they are separated out.
Those services are organized into logical groups, and then a single svchost.exe instance is created for each group. For instance, one svchost.exe instance runs the 3 services related to the firewall. Another svchost.exe instance might run all the services related to the user interface, and so on.
So What Can I Do About It?
You can trim down unneeded services by disabling or stopping the services that don’t absolutely need to be running. Additionally, if you are noticing very heavy CPU usage on a single svchost.exe instance you can restart the services running under that instance.
The biggest problem is identifying what services are being run on a particular svchost.exe instance… we’ll cover that below.
How to resize the edit text box in Google blogger
Sunday, October 18, 2009
TCP and UDP Ports Explained
(copied from http://www.bleepingcomputer.com/tutorials/tutorial38.html)
Introduction
In this tutorial we will discuss the concept of Ports and how they work with IP addresses. If you have not read our article on IP addresses and need a brush up, you can find the article here. If you understand the concepts of IP addresses, then lets move on to TCP and UDP ports and how they work.
The devices and comptuers connected to the Internet use a protocol called TCP/IP to communicate with each other. When a computer in New York wants to send a piece of data to a computer in England, it must know the destination IP address that it woud like to send the information to. That information is sent most often via two methods, UDP and TCP.
The two Internet workhorses: UDP and TCP
UDP? TCP? I know you are getting confused, but I promise I will explain this in very basic terms so that you can understand this concept.
TCP stands for Transmission Control Protocol. Using this method, the computer sending the data connects directly to the computer it is sending the data it to, and stay connected for the duration of the transfer. With this method, the two computers can guarantee that the data has arrived safely and correctly, and then they disconnect the connection. This method of transferring data tends to be quicker and more reliable, but puts a higher load on the computer as it has to monitor the connection and the data going across it. A real life comparison to this method would be to pick up the phone and call a friend. You have a conversation and when it is over, you both hang up, releasing the connection.
UDP stands for User Datagram Protocol. Using this method, the computer sending the data packages the information into a nice little package and releases it into the network with the hopes that it will get to the right place. What this means is that UDP does not connect directly to the receiving computer like TCP does, but rather sends the data out and relies on the devices in between the sending computer and the receiving computer to get the data where it is supposed to go properly. This method of transmission does not provide any guarantee that the data you send will ever reach its destination. On the other hand, this method of transmission has a very low overhead and is therefore very popular to use for services that are not that important to work on the first try. A comparison you can use for this method is the plain old US Postal Service. You place your mail in the mailbox and hope the Postal Service will get it to the proper location. Most of the time they do, but sometimes it gets lost along the way.
Now that you understand what TCP and UDP are, we can start discussing TCP and UDP ports in detail. Lets move on to the next section where we can describe the concept of ports better.
TCP and UDP Ports
As you know every computer or device on the Internet must have a unique number assigned to it called the IP address. This IP address is used to recognize your particular computer out of the millions of other computers connected to the Internet. When information is sent over the Internet to your computer how does your computer accept that information? It accepts that information by using TCP or UDP ports.
An easy way to understand ports is to imagine your IP address is a cable box and the ports are the different channels on that cable box. The cable company knows how to send cable to your cable box based upon a unique serial number associated with that box (IP Address), and then you receive the individual shows on different channels (Ports).
Ports work the same way. You have an IP address, and then many ports on that IP address. When I say many, I mean many. You can have a total of 65,535 TCP Ports and another 65,535 UDP ports. When a program on your computer sends or receives data over the Internet it sends that data to an ip address and a specific port on the remote computer, and receives the data on a usually random port on its own computer. If it uses the TCP protocol to send and receive the data then it will connect and bind itself to a TCP port. If it uses the UDP protocol to send and receive data, it will use a UDP port. Figure 1, below, is a represenation of an IP address split into its many TCP and UDP ports. Note that once an application binds itself to a particular port, that port can not be used by any other application. It is first come, first served.
<-------------------- 192.168.1.10 -------------------->
0 | 1 | 2 | 3 | 4 | 5 | .. | .. | .. | .. | .. | .. | .. | .. | 65531 | 65532 | 65533 | 65534 | 65535 | ||||||||||||
Figure 1. IP address with Ports
This all probably still feels confusing to you, and there is nothing wrong with that, as this is a complicated concept to grasp. Therefore, I will give you an example of how this works in real life so you can have a better understanding. We will use web servers in our example as you all know that a web server is a computer running an application that allows other computers to connect to it and retrieve the web pages stored there.
In order for a web server to accept connections from remote computers, such as yourself, it must bind the web server application to a local port. It will then use this port to listen for and accept connections from remote computers. Web servers typically bind to the TCP port 80, which is what the http protocol uses by default, and then will wait and listen for connections from remote devices. Once a device is connected, it will send the requested web pages to the remote device, and when done disconnect the connection.
On the other hand, if you are the remote user connecting to a web server it would work in reverse. Your web browser would pick a random TCP port from a certain range of port numbers, and attempt to connect to port 80 on the IP address of the web server. When the connection is established, the web browser will send the request for a particular web page and receive it from the web server. Then both computers will disconnect the connection.
Now, what if you wanted to run an FTP server, which is a server that allows you to transfer and receive files from remote computers, on the same web server. FTP servers use TCP ports 20 and 21 to send and receive information, so you won't have any conflicts with the web server running on TCP port 80. Therefore, the FTP server application when it starts will bind itself to TCP ports 20 and 21, and wait for connections in order to send and receive data.
Most major applications have a specific port that they listen on and they register this information with an organization called IANA. You can see a list of applications and the ports they use at the IANA Registry. With developers registering the ports their applications use with IANA, the chances of two programs attempting to use the same port, and therefore causing a conflict, will be diminished.
--------------------- o0o ---------------------
























