using System.IO;
using System.Xml.Serialization;
public void SerializeObject(string filename, PersonnelService.PersonnelInput objectToSerialize)
{
Stream stream = File.Open(filename, FileMode.Create);
XmlSerializer ser = new XmlSerializer(typeof(PersonnelService.PersonnelInput));
ser.Serialize(stream, objectToSerialize);
stream.Close();
}
Friday, October 30, 2009
Serialize Object To File
Thursday, October 29, 2009
Wednesday, October 28, 2009
How to deploy a web application to Weblogic
Tuesday, October 27, 2009
Ringtone converter: from and to .amr file
Saturday, October 24, 2009
How to know the web server type
Want to know where is the location of a server
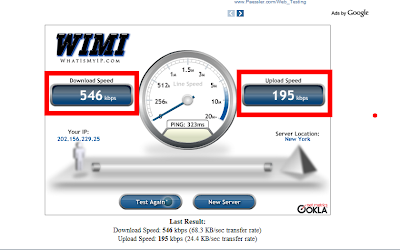
How to test your internet speed
2. Choose a server and click test
3. Wait for about less than 1 minute and see the result
Thursday, October 22, 2009
Oracle - Add new column to a table
ADD ( "TEAM" VARCHAR2(2) DEFAULT 'AT' )
Wednesday, October 21, 2009
Common processes
The process lsass.exe serves as the Local Security Authentication Server by Microsoft, Inc. It is responsible for the enforcement of the security policy within the operating system. This process checks whether a user’s supplied identification is valid or not whenever he or she tries to access the computer system.
With the execution of the file lsass.exe, the system acquires security by preventing the access of unwanted users to any private information. The file lsass.exe also handles the password modifications done by the user.
Local Session Manager. Process found on Windows Vista and whose role is to manage the terminal server connections to the machine. In Vista, terminal server sessions are not just Remote Desktop sessions from remote users as they are in Windows XP/2003, they are also your sessions when you are logged in to the PC at the PC itself, as all sessions, whether local or remote, are virtualised terminal server sessions. It follows, therefore, that this process is a crucial core process of Windows Vista.
is a process belonging to the Windows login manager. It handles the login and logout procedures on your system. This program is important for the stable and secure running of your computer and should not be terminated
is a part of the Microsoft Windows Operating System and manages the operation of starting and stopping services. This process also deals with the automatic starting of services during the computers boot-up and the stopping of services during shut-down. This program is important for the stable and secure running of your computer and should not be terminated.
This is a system critical process, as long as it exists in %windir%\system32. Its job is to start some of the core Windows Vista background services.
The Microsoft Client Server Runtime Server subsystem utilizes the process csrss.exe for managing the majority of the graphical instruction sets under the Microsoft Windows operating system. As such Csrss.exe provides the critical functions of the operating system, and its termination can result in the Blue Screen of Death being displayed.
Csrss.exe controls threading and Win32 console window features. Threading is where the application splits itself into multiple simultaneous running tasks. Threads supported by csrss.exe are different from processes in that threads are commonly contained within the process, with various threads sharing resources within the same process. The Win32 console is the plain text window in the Windows API system (programs can use the console without the need for image display).
In mobile devices such as notebooks and laptops, the process csrss.exe is closely dependent on power management schemes implemented by the system as defined under the Control Panel option.
The Session Manager Subsystem is responsible for starting a user's session. When this process begins, the system thread is responsible for a number of specific tasks including launching the Winlogon, specific Win32 processes and among other items, setting the system variables.
Many computer users first notice the SMSS.exe process when a system shuts down abnormally. For instance, when a Winlogon ends normally, this process usually has no problem fulfilling its tasks, however, when a system shuts down abnormally or unexpectedly, the SMSS.exe causes a "hang" which is when the system stops responding.
Tuesday, October 20, 2009
Screen recorder
2. Screen capture

3. Download link:
- From wareseeker: http://wareseeker.com/download/oripa-screen-recorder-1.2.2.rar/416172
- I've downloaded and uploaded to the following location: http://cid-194a44aed6d769a5.skydrive.live.com/self.aspx/.Public/oRipa%5E_Screen%5E_Recorder.msi
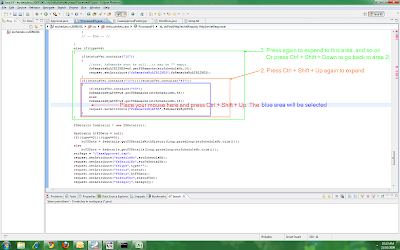
Eclipse - how to select enclosed element
2. Press Alt + Shift + Up to expand the selection
3. Press Alt + Shift + Down to collapse the selection
* The image below is wrong (Alt instead of Ctrl)
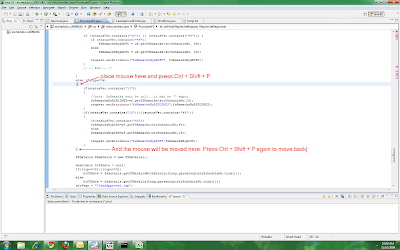
Eclipse - how to find the match brace
2. Press Ctrl + Shift + P to jump to the match brace
3. Press Ctrl + Shift + P again to jump back.
Monday, October 19, 2009
Useful windows command
- http://commandwindows.com/doskey.htm
- tasklist /svc list all services which are running
- netstat -n -a list all port which are in using
- msinfo32 system information
- tracert The actual path between two computers on the Internet
- pathping combine ping and tracert
- nslookup diagnose the Domain Name System (DNS) infrastructure and comes with a number of sub-commands
- netsh The network services shell is a large suite of many tools
What is svchost.exe And Why Is It Running?
What is svchost.exe And Why Is It Running?
You are no doubt reading this article because you are wondering why on earth there are nearly a dozen processes running with the name svchost.exe. You can’t kill them, and you don’t remember starting them… so what are they?
So What Is It?
According to Microsoft: “svchost.exe is a generic host process name for services that run from dynamic-link libraries”. Could we have that in english please?
Some time ago, Microsoft started moving all of the functionality from internal Windows services into .dll files instead of .exe files. From a programming perspective this makes more sense for reusability… but the problem is that you can’t launch a .dll file directly from Windows, it has to be loaded up from a running executable (.exe). Thus the svchost.exe process was born.
Why Are There So Many svchost.exes Running?
If you’ve ever taken a look at the Services section in control panel you might notice that there are a Lot of services required by Windows. If every single service ran under a single svchost.exe instance, a failure in one might bring down all of Windows… so they are separated out.
Those services are organized into logical groups, and then a single svchost.exe instance is created for each group. For instance, one svchost.exe instance runs the 3 services related to the firewall. Another svchost.exe instance might run all the services related to the user interface, and so on.
So What Can I Do About It?
You can trim down unneeded services by disabling or stopping the services that don’t absolutely need to be running. Additionally, if you are noticing very heavy CPU usage on a single svchost.exe instance you can restart the services running under that instance.
The biggest problem is identifying what services are being run on a particular svchost.exe instance… we’ll cover that below.
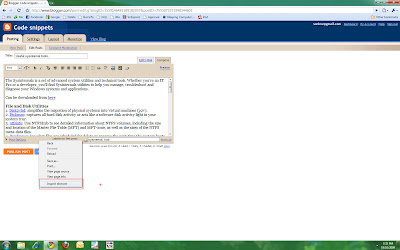
How to resize the edit text box in Google blogger
Sunday, October 18, 2009
TCP and UDP Ports Explained
(copied from http://www.bleepingcomputer.com/tutorials/tutorial38.html)
Introduction
In this tutorial we will discuss the concept of Ports and how they work with IP addresses. If you have not read our article on IP addresses and need a brush up, you can find the article here. If you understand the concepts of IP addresses, then lets move on to TCP and UDP ports and how they work.
The devices and comptuers connected to the Internet use a protocol called TCP/IP to communicate with each other. When a computer in New York wants to send a piece of data to a computer in England, it must know the destination IP address that it woud like to send the information to. That information is sent most often via two methods, UDP and TCP.
The two Internet workhorses: UDP and TCP
UDP? TCP? I know you are getting confused, but I promise I will explain this in very basic terms so that you can understand this concept.
TCP stands for Transmission Control Protocol. Using this method, the computer sending the data connects directly to the computer it is sending the data it to, and stay connected for the duration of the transfer. With this method, the two computers can guarantee that the data has arrived safely and correctly, and then they disconnect the connection. This method of transferring data tends to be quicker and more reliable, but puts a higher load on the computer as it has to monitor the connection and the data going across it. A real life comparison to this method would be to pick up the phone and call a friend. You have a conversation and when it is over, you both hang up, releasing the connection.
UDP stands for User Datagram Protocol. Using this method, the computer sending the data packages the information into a nice little package and releases it into the network with the hopes that it will get to the right place. What this means is that UDP does not connect directly to the receiving computer like TCP does, but rather sends the data out and relies on the devices in between the sending computer and the receiving computer to get the data where it is supposed to go properly. This method of transmission does not provide any guarantee that the data you send will ever reach its destination. On the other hand, this method of transmission has a very low overhead and is therefore very popular to use for services that are not that important to work on the first try. A comparison you can use for this method is the plain old US Postal Service. You place your mail in the mailbox and hope the Postal Service will get it to the proper location. Most of the time they do, but sometimes it gets lost along the way.
Now that you understand what TCP and UDP are, we can start discussing TCP and UDP ports in detail. Lets move on to the next section where we can describe the concept of ports better.
TCP and UDP Ports
As you know every computer or device on the Internet must have a unique number assigned to it called the IP address. This IP address is used to recognize your particular computer out of the millions of other computers connected to the Internet. When information is sent over the Internet to your computer how does your computer accept that information? It accepts that information by using TCP or UDP ports.
An easy way to understand ports is to imagine your IP address is a cable box and the ports are the different channels on that cable box. The cable company knows how to send cable to your cable box based upon a unique serial number associated with that box (IP Address), and then you receive the individual shows on different channels (Ports).
Ports work the same way. You have an IP address, and then many ports on that IP address. When I say many, I mean many. You can have a total of 65,535 TCP Ports and another 65,535 UDP ports. When a program on your computer sends or receives data over the Internet it sends that data to an ip address and a specific port on the remote computer, and receives the data on a usually random port on its own computer. If it uses the TCP protocol to send and receive the data then it will connect and bind itself to a TCP port. If it uses the UDP protocol to send and receive data, it will use a UDP port. Figure 1, below, is a represenation of an IP address split into its many TCP and UDP ports. Note that once an application binds itself to a particular port, that port can not be used by any other application. It is first come, first served.
<-------------------- 192.168.1.10 -------------------->
0 | 1 | 2 | 3 | 4 | 5 | .. | .. | .. | .. | .. | .. | .. | .. | 65531 | 65532 | 65533 | 65534 | 65535 | ||||||||||||
Figure 1. IP address with Ports
This all probably still feels confusing to you, and there is nothing wrong with that, as this is a complicated concept to grasp. Therefore, I will give you an example of how this works in real life so you can have a better understanding. We will use web servers in our example as you all know that a web server is a computer running an application that allows other computers to connect to it and retrieve the web pages stored there.
In order for a web server to accept connections from remote computers, such as yourself, it must bind the web server application to a local port. It will then use this port to listen for and accept connections from remote computers. Web servers typically bind to the TCP port 80, which is what the http protocol uses by default, and then will wait and listen for connections from remote devices. Once a device is connected, it will send the requested web pages to the remote device, and when done disconnect the connection.
On the other hand, if you are the remote user connecting to a web server it would work in reverse. Your web browser would pick a random TCP port from a certain range of port numbers, and attempt to connect to port 80 on the IP address of the web server. When the connection is established, the web browser will send the request for a particular web page and receive it from the web server. Then both computers will disconnect the connection.
Now, what if you wanted to run an FTP server, which is a server that allows you to transfer and receive files from remote computers, on the same web server. FTP servers use TCP ports 20 and 21 to send and receive information, so you won't have any conflicts with the web server running on TCP port 80. Therefore, the FTP server application when it starts will bind itself to TCP ports 20 and 21, and wait for connections in order to send and receive data.
Most major applications have a specific port that they listen on and they register this information with an organization called IANA. You can see a list of applications and the ports they use at the IANA Registry. With developers registering the ports their applications use with IANA, the chances of two programs attempting to use the same port, and therefore causing a conflict, will be diminished.
--------------------- o0o ---------------------
Saturday, October 17, 2009
Manage port/firewall
- http://msdn.microsoft.com/en-us/library/cc646023.aspx
- netstat –n –a
- PortQry tool
- WF.msc (firewall rule)
- netsh firewall set portopening protocol = TCP port = 1433 name = SQLPort mode = ENABLE scope = SUBNET profile = CURRENT
- firewall.cpl
Tools
- Performent analysis
- DTCPing Tool to troubleshoot DTC firewall problem.
- Windows XP small tools
- Anti-virus Portable ClamWin
- Portable Free Download Manager
- Video converter - Format Factory Portable
- FFmpeg - record, convert and stream audio and video
- VLC Media Player – A Multi-platform Multimedia Player
- PhotoFiltre – A Complete Image Retouching Program
- CDBurnerXP - Disc burning app for your USB flash drive
- InfraRecorder Portable to burn DVD
WCF SAP Adapter Error: Incorrect Action
An error occurred during calling an RFC / TRfc / BAPI to SAP
Incorrect Action http://Microsoft.LobServices.Sap/2007/03/blablabla . Correct the specified Action, or refer to the documentation on the allowed formats for the Actions.
This problem occur for only two reason:
The WCF SAP Adapter using WCF Custom adapter, the important thing is the SOAP Action Header under General Tab in Configuration.
this is a sample of SOAP Header:
<BtsActionMapping xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<Operation Name="Z_BAPI_PIP3B2_INBOUND" Action="http://Microsoft.LobServices.Sap/2007/03/Rfc/Z_BAPI_PIP3B2_INBOUND" />
</BtsActionMapping>
Name parameter correspond to the Operation of the logical orchestration port and Action usually correspond to MessageType without #.
This is default using from adapter wizard.
To be sure to do all correctly you can do that:
Import schema from SAP, after you'll find a Bindinginfo file to create a physical port on BizTalk from admin console.
Open this file and use the value of action paramenter to rename the operation of orchestration logical port.
Deploy all, create physical port with binding file and configure your orchestration.
You could use a your custom action, to do that write WCF.Action context property:
myMessage(WCF.Action)="http://myAction/asd.asd.asd"
This is a grate thing to use multiple operation on a single port
BizTalk troubleshooting
- BAM Web Services and SQL Server mixed mode authentication : http://blogs.msdn.com/tihot/archive/2006/06/13/630313.aspx
- BAM troubeshooting
Please logon local to your BAM Portal server and check the following:
- Open IE and navigate to the BAM Portal for example like this: http://localhost/bam/BamManagementService/BamManagementService.asmx
If it works, your web service is working. - Click: GetViewSummaryForCurrentUser
- Press the Invoke button, displayed in the upper left corner
- If it works, your web service is able to talk to the database
- If it does not work, check the web.config file under for example
C:\Program Files (x86)\Microsoft BizTalk Server 2006\BAMPortal\BAMManagementService
- If it works, your web service is able to talk to the database
<appSettings>
<add key="BamServer" value="SKLAB5026" />
<add key="BamDatabase" value="BAMPrimaryImport" />
</appSettings>
Make sure the correct database server and name is entered. Also check the web.config file of the BAMQueryService as well.
- BizTalk Adapter Package version
ProductVersion for that adapter (most probably under): "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\BizTalk Adapter.."
- How TPE log the data to PrimaryImport DB
To be more precise, TPE utilize OrchestrationEventStream to log data to the messagebox.
Later, the TDDS writes data to the PrimaryImport database…
- About DehydrationFailedException: The string '' is not a valid AllXsd value.
This is a serialization issue. While dehydrating, engine tries to serialize objects – apparently in the orchestration code there are some objects being used which are not serializable. We advice to use Atomic Shape in such cases so that orchestration does not dehydrate.
- Set up a Windows Server Cluster on Hyper-V virtual machines using iSCSI for storage (see http://blogs.technet.com/pfe-ireland/archive/2008/05/16/how-to-create-a-windows-server-2008-cluster-within-hyper-v-using-simulated-iscsi-storage.aspx)
- You can see the whitepaper for the BizTalk Adapter pack to get an idea of what the supported scenarios are.
- Since everything is SSL-encrypted I used the .Net tracing from here: http://blogs.msdn.com/dgorti/archive/2005/09/18/471003.aspx
- How to monitor BizTalk performent: http://msdn.microsoft.com/en-us/library/aa578302.aspx
- Creating, Updating, and Deleting a Host Instance Using WMI: http://msdn.microsoft.com/en-in/library/aa560467(en-us).aspx
- BizTalk performent: http://www.unisys.com/eprise/main/admin/corporate/doc/BL100200.pdf
- Keperos in Sharepoint: http://www.windowsecurity.com/articles/Kerberos-Sharepoint-Environment.html
- BizTalk Server Database Optimization: http://msdn.microsoft.com/en-us/library/bb743398.aspx
Chrome - I’m feeling lucky
- Click the Wrench icon, select Options
- On the Basics tab at Default Search, click Manage
- Click Add
- On Name: let's label it as "I'm Feeling Lucky"
- On URL: right-click on the link below and select Copy Link Address and paste it.
- where, btnl=745 acts as I'm Feeling Lucky in Google's search engine
- Click OK to confirm
- Select your "I'm Feeling Lucky" and Make Default
- Close
SharePoint - Delete Library List
- Click to go to the item to be deleted
- Select Form Library Settings in Settings menu
- Click “Delete this form library”



Wednesday, October 14, 2009
My top ten computer favourites - Oct 2009
- Picasa
- Window Commander
- Linux
- Chrome/Firefox
- Visual Studio/Eclipse
- blogger
- gmail
- VNC
- ZoomIt
- ThunderBird
My favourite web sites
- NirSoft - freeware utilities: password recovery, system utilities, desktop utilities
- Sysinternal - Advance utilities for windows
- Apache
- Open source projects
- Java blog
- Photo collections
- Popular Images
- Bookmarking images.
- Comments for MySpace, Hi5 and Orkut
- http://www.glitter-graphics.com/
- http://www.myhotcomments.com/
- Sign generator
- http://lifehacker.biz/
- Bittorrent sites
- Vietnamese Unicode link
How to turn off firewall in Windows 7
- Download and install process hacker (which can be found in here)
- Open Process Hacker --> Service tab
- Kill all processes which have description contains firewall
ZoomIt - simple utility for zooming and drawing on the screen
.jpg)
Tuesday, October 13, 2009
Install BizTalk MQSC Adapter on 64-bit Windows
- The MQSC Adapter only supports 32-bit versions of Microsoft Windows that are supported by BizTalk Server 2006. WebSphere MQ on Windows is not supported on 64-bit versions of Windows. Therefore, the MQSC Adapter is not supported on a 64-bit version of Windows or on a 32-bit BizTalk host instance that is running in a 64-bit version of Windows.
- An update is available that enables you to install the client-based BizTalk Adapter for WebSphere MQ on 64-bit versions of Windows: http://support.microsoft.com/kb/939202
- To obtain this feature immediately, you need to contact Microsoft Customer Support Services to get the file.
- I've updated the update to internet. If you want to try, can get it from here
Useful sysinternal tools.
- Disk2vhd: simplifies the migration of physical systems into virtual machines (p2v).
- Diskmon: captures all hard disk activity or acts like a software disk activity light in your system tray.
- ntfsinfo: Use NTFSInfo to see detailed information about NTFS volumes, including the size and location of the Master File Table (MFT) and MFT-zone, as well as the sizes of the NTFS meta-data files.
- Pendmove: See what files are scheduled for delete or rename the next time the system boots.
- Process Monitor: Monitor file system, Registry, process, thread and DLL activity in real-time.
- psfile: See what files are opened remotely.
- pstool: The PsTools suite includes command-line utilities for listing the processes running on local or remote computers, running processes remotely, rebooting computers, dumping event logs, and more.
- PsExec - execute processes remotely
- PsFile - shows files opened remotely
- PsGetSid - display the SID of a computer or a user
- PsInfo - list information about a system
- PsKill - kill processes by name or process ID
- PsList - list detailed information about processes
- PsLoggedOn - see who's logged on locally and via resource sharing (full source is included)
- PsLogList - dump event log records
- PsPasswd - changes account passwords
- PsService - view and control services
- PsShutdown - shuts down and optionally reboots a computer
- PsSuspend - suspends processes
- SDelete: Securely overwrite your sensitive files and cleanse your free space of previously deleted files using this DoD-compliant secure delete program.
- sigcheck: Dump file version information and verify that images on your system are digitally signed.
- Sync: Flush cached data to disk. This tool can be used before removing your thump drive
- Autoruns: See what programs are configured to startup automatically when your system boots and you login.
- Handle: This handy command-line utility will show you what files are open by which processes, and much more. Use Process Expolorer for the UI version.
- ListDll: List all the DLLs that are currently loaded, including where they are loaded and their version numbers. Version 2.0 prints the full path names of loaded modules.
- Process Explorer: Find out what files, registry keys and other objects processes have open, which DLLs they have loaded, and more. This uniquely powerful utility will even show you who owns each process.
- Process Monitor: Monitor file system, Registry, process, thread and DLL activity in real-time.
- ShellRunas: Launch programs as a different user via a convenient shell context-menu entry
- VMMap: See a breakdown of a process's committed virtual memory types as well as the amount of physical memory (working set) assigned by the operating system to those types. Identify the sources of process memory usage and the memory cost of application features.
Monday, October 12, 2009
Format SQL statement

1. Open Aqua Data Studio which is can be downloaded here.
Monday, October 5, 2009
Eclipse shortcut keys
- How to view/modify shortcuts in eclipse (version 3.4.2): Windows --> Preferences --> General --> Keys
- Delete a line: Ctrl + D
- Active editor: F12
- Find and replace: Ctrl + F
- Incremental find: Ctrl + J
- Duplicate lines: Ctrl + Alt + Down




















